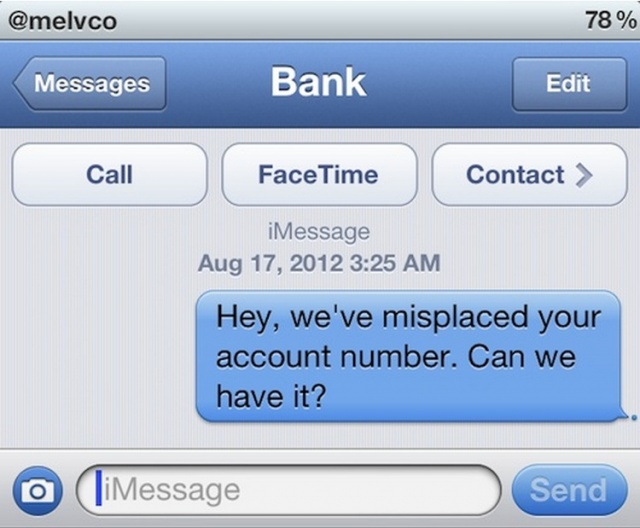
It appears Apple’s arrogance is getting in the way of protecting its users from a long standing SMS exploit that could allow potential hackers to spoof a reply-to number, causing the recipient to think he/she is replying to a legitimate contact, when in reality, their information is being sent to the hackers designated address. As you can imagine, this is quite troublesome, yet Apple has brushed it away despite numerous pleas made by a well known iOS hacker (pod2g):
If you’ve been following up on the Black Hat conference going on in Las Vegas, you may have heard about how NFC can be used to execute malicious code on an Android device. While the hack, demonstrated by security researcher Charlie Miller, does expose an issue with the way Android should handle NFC commands, it’s likely to result in more good than it is actual harm.
I smell a FUD storm a brewin’ and I’m sure Apple blogs will be foaming at the mouths in the next 24 hours. According to the security research firm SpiderLabs, they were able to submit an SMS app to the Google Play Store and then update it incrementally to turn it malicious without triggering Bouncer: Android’s malware detection system.

Boeing has announced plans to manufacture secure Android devices for U.S. government defense and security markets and you can bet your tax paying dollars these handsets will put carrier pricing to shame. Roger Krone, president of Boeing Network and Space Systems, was quoted as saying that Beoing was aiming to launch the device in late 2012, at a lower price than competitors who sell secure phones for as much as $20,000. Yep, you read that right, our government is paying upwards of $20,000 for a secure phone (talk about an expensive incognito mode).

We’re always hearing about possible Android malware and whether or not it’s simply FUD, we’re here to report it and remind you of the common-sense ways of protecting yourself. The latest Android malware scare comes to us from security research company NQ Mobile. According to NQ Mobile, their research has uncovered a new UpdtBot malware application file that is disguising itself as a system upgrade. NQ Mobile reports more than 160,000 Android users have been affected by UpdtBot and that it is spreading via SMS messages. Once installed, UpdtBot registers a remote Command and Control (C&C) server, which instructs the infected device to send text messages, make phone calls, and download and install apps.