Beware new Android malware disguised as classic Nintendo games

Not all Mario is good. Screenshot: Nintendo
One of the biggest reasons to choose Android over other platforms is the ability to play classic console games with the help of an emulator. But you should be careful when searching for your next one, because there’s new Android malware out there that disguises itself as retro Nintendo games.
Discovered by researchers at Palo Alto Networks, the new malware family named “Gunpoder” has the ability to collect sensitive information, execute malicious code, push fraudulent adverts, and more. It has been targeting Android users in 13 countries, including the U.S.
The researchers report that Gunpoder shares similar traits with adware, which isn’t normally blocked by antivirus products, including genuine ads. But it does much more than display a few popups in the hope that you’ll install an app or hand over some cash.
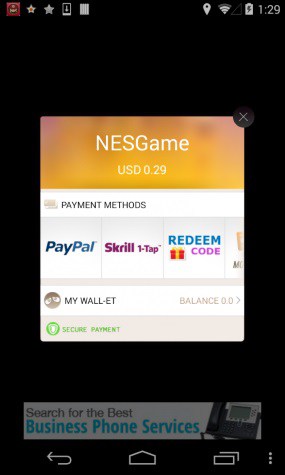
Screenshot: Palo Alto Networks
“While researching the sample, we observed that while it contained many characteristics of adware, and indeed embeds a popular adware library within it, a number of overtly malicious activities were also discovered, which we believe characterizes this family as being malware,” reads the report.
Gunpoder is disguised as Nintendo Entertainment System (NES) emulator, but when opened for the first time, it displays a popup that asks users to pay for lifetime ownership. If you hit the “Great! Certainly!” button, you are prompted to pay $0.29 or $0.49 using PayPal, Skrill, Xsolla, or CYPay.
The popup also appears when you attempt to access the emulator’s “Cheats” function, and if you don’t pay up, you will be prompted to share a “fun game” with a friend instead. However, the SMS actually contains a link to more Gunpoder malware.
Gunpoder also has the ability to send SMS messages in the background, without a users’ knowledge… unless you live in China.
“Interestingly enough, the Gunpoder sample will detect the country of the user,” explains Palo Alto Networks. “If the user is not located in China, this app will automatically send an SMS message, which contains a variant downloading link, to random selected friends in the background.”
And that’s not all. Gundoper can also direct users to fraudulent ads, collect sensitive data from your device, and execute other payloads. In other words, it has the ability to install more malware and malicious code without the users’ input.
Gunpoder’s creator used an open-source NES emulator framework to fool Android users into thinking they were getting a genuine NES emulator. So far, Palo Alto Networks has discovered 49 unique samples of the malware out in the wild.
You can protect yourself by only installing trusted apps, and steering clear of those from unknown developers that don’t appear to be genuine. You can also use antivirus software on your Android device for added peace of mind.
As you might expect, Palo Alto Networks’ own WildFire, Threat Prevention, and Mobile Security Manager software has already been updated to detect Gunpoder, and we expect other antivirus vendors to follow suit.
- SourcePalo Alto Networks
- ViaNDTV


