Pimpin’ Ain’t Easy… Unless You Have An Android Phone With Pattern Lock
When we think about security for our mobile devices, we’re usually protecting it from nefarious individuals. Well guess what? It apparently works both ways. In a story straight out of James Brown’s diary, the FBI is having a hard time busting a notorious San Diego pimp thanks to Android’s pattern lock feature.
After numerous arrests and jail time, Dante Dears — founder and head of “Pimpin’ Hoes Daily” (I’m not making this up) — found himself out on parole, shackled with a GPS monitor, and ordered to stay off the streets. He of course learned his lesson and gave up found craftier ways to run his hoe empire. Giving orders and setting up tricks via a Samsung Android phone, Dante Dears had women dropping off cash in fear of getting mobile bitch slapped.
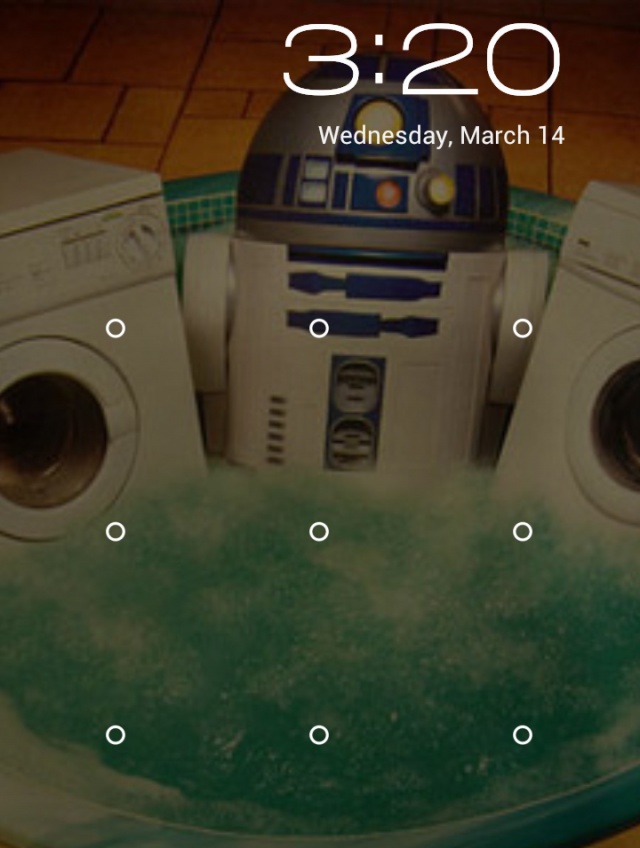
After hours of surveillance and undercover work, FBI agents confronted Dears with the evidence and he quickly fessed up denied the allegations stating that the cellphone belonged to his sister. He eventually gave up the phone but being the security conscious pimp that he was, he had it protected with Android’s pattern lock feature — a feature which requires the user to drag a preset pattern across the unlock grid to gain access to the device.
The FBI sent the phone off to the FBI Regional Computer Forensics Lab in Southern California where technicians were defeated by the pattern lock and eventually locked out completely due to too many failed attempts. Since the device now requires Dears’ Google account credentials (which he isn’t giving up), the FBI is looking to Google to help them out. In a new warrant filed with the judge, the FBI asks Google to hand over:
- The subscriber’s name, address, Social Security number, account login and password
- “All e-mail and personal contact list information on file for cellular telephone”
- The times and duration of every webpage visited
- All text messages sent and received from the phone, including photo and video messages
- Any e-mail addresses or instant messenger accounts used on the phone
- “Verbal and/or written instructions for overriding the ‘pattern lock’ installed on the” phone
- All search terms, Internet history, and GPS data that Google has stored for the phone
There’s been no word from Google regarding the warrant or whether or not they will comply, but if we’ve learned one thing from this crazy ordeal, it’s that Pimpin’ ain’t easy… unless you have an Android phone with pattern lock.
Update: Google has provided ars technica with a general statement:
“Like all law-abiding companies, we comply with valid legal process. Whenever we receive a request we make sure it meets both the letter and spirit of the law before complying. If we believe a request is overly broad, we will seek to narrow it.”
- Sourcears technica


